Cloud Native Security
Advanced protection for cloud hosts and containers, optimized for DevSecOps workflows.
Call a Specialist Today! 888-785-4405 | Free Shipping!

High-impact protection with low impact on performance for on-premise, data center, and cloud workloads

Advanced protection for cloud hosts and containers, optimized for DevSecOps workflows.
Get complete visibility of suspicious activity across your entire IT environment.
Elite team of MDR threat hunters and response experts who take targeted actions on your behalf to neutralize even the most sophisticated threats.
Artificial intelligence built into Intercept X that detects both known and unknown malware without relying on signatures
Deny attackers by blocking the exploits and techniques used to distribute malware, steal credentials, and escape detection.
Elite team of MDR threat hunters and response experts who take targeted actions on your behalf to neutralize even the most sophisticated threats.
Prevent unauthorized programs running on your servers and receive notification if attempts are made to tamper with critical files.
Identify sophisticated attacks as they happen without requiring a kernel module, orchestration, baselining, or system scans.
Behavioral and exploit runtime detections identify threats including container escapes, kernel exploits, and privilege escalation.
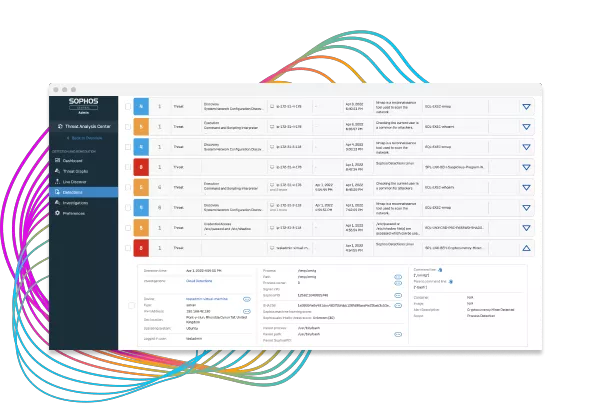
Sophos Cloud Workload Protection provides complete visibility into your host and container workloads, identifying malware, exploits, and anomalous behavior before they get a foothold.
Flexible, lightweight server host and container protection is optimized for performance. Available as an agent or via API for Linux to integrate with your security operations, IT, and DevOps processes.

Secure the host and container with an agent managed from the Sophos Central management console. Easily investigate and respond to behavioral, exploit, and malware threats in one place while increasing IT hygiene with automated detections, intuitive querying, and remote response capabilities.
Fine-tuned for maximum performance, seamlessly enrich your security operations workflows with an ultra-lightweight Linux sensor providing API integration of host and container behavioral and exploit runtime detections into your existing automation, orchestration, log management, and incident response tooling.
As your organization expands from on-premises or data center to hybrid and multi-cloud environments, Sophos protects your infrastructure and data across deployment and computing models.
Detection and resilience for Linux systems in any environment, including container runtimes such as Docker, containerd, and CRI-O. Our detection is crafted with the threat models of cloud-native systems in mind.
Secure your Windows hosts and remote workers against ransomware, exploits and never-before-seen threats, control applications, lockdown good configurations, and monitor changes to critical system files.
Secure applications and data across your hybrid cloud footprint from a single console. The flexible agent runs on-premises, in data centers, hybrid and multi-cloud environments including AWS, Azure, GCP and Oracle Cloud.
Sophos Workload Protection uses deep learning, an advanced form of machine learning that detects both known and unknown malware without relying on signatures.
Deep learning makes Sophos Workload Protection smarter, more scalable, and more effective against never-seen-before threats, outperforming security solutions that use traditional machine learning or signature-based detection alone.

Sophos Workload Protection includes unique CryptoGuard technology that universally detects and stops ransomware before it can impact your server workloads, including new variants and both local and remote ransomware attacks.
Using advanced mathematical analysis of file contents, CryptoGuard detects malicious encryption wherever it takes place. Any maliciously encrypted files are automatically rolled back to their unencrypted state, irrespective of size or file type, minimizing the business impact.
Sophos XDR is the industry's only security operations platform that brings together native workload protection, endpoint, firewall, email, cloud security, and third-party security controls. Get a holistic view of your organization's environment enriched with Sophos X-Ops threat intelligence for detection, investigation, and response designed for dedicated SOC teams and IT admins.
Proactive 24/7 hunting by our elite team of threat analysts. Determine the potential impact and context of threats to your business
Get actionable advice for addressing the root cause of recurring incidents to stop them from occurring again
Initiates actions to remotely disrupt, contain and neutralize threats on your behalf to stop even the most sophisticated threats